Protected Business Connectivity
Your IT partner for a connected and secure future

Delivering Outstanding Customer Service and Comprehensive IT Solutions
Protecting Your Business from Cyber Threats with Tailored Cybersecurity Solutions and Proactive Defense Strategies.
Efficiently Managing Your IT Infrastructure with Proactive Support: Partner with us for Reliable and Scalable Managed IT Solutions.
Design a Secured Network with Next-Gen Firewalls, Network Monitoring & Security. Thrive in a secure and efficient network environment.

Partnering for Peace of Mind
Empowering Success: Exceptional IT Support and Cybersecurity Mastery. We offer a comprehensive suite of IT services, ensuring seamless operations, minimal interruptions, and optimal productivity for your business. From robust cybersecurity solutions and managed IT support to data recovery and Office 365 assistance, we’ve got you covered. Our commitment is to your peace of mind, allowing you to focus on what you do best – running your business, while we take care of your technology needs.
Your Digital Partners: Beyond IT Solutions, Exceptional Service, Embrace Technology Together
CyberGuard
Empower your business with tailored cybersecurity solutions and proactive defense against cyber threats with CyberGuard.
IT solutions
Empower your business with proactive IT support and reliable managed solutions offered by ProTech Solutions.
Data Guard
Safeguard your valuable data and ensure business continuity with expert data recovery services from DataGuard, your trusted restoration partner.
Office 365
Empower your productivity with OfficeMax, unlocking the full potential of Office 365 through seamless migration and enhanced collaboration tools.
Backup & Recovery
Ensure business continuity and minimize downtime with ResilientGuard's robust backup and disaster recovery solutions, maximizing your organization's resilience.
Telecoms
Revolutionize global communication, connecting people, businesses, and societies, fostering collaboration and enabling rapid information exchange
Continuous security
The company’s uninterrupted security has helped to maintain its reputation for reliability.
Step 02
Deep Penetration Testing
Scan & Penetration Testing & Comprehensive Security Assessment
Step 03
Solution-Oriented Reporting
Detailed Findings and Solution Proposals
Cyber Security
Full penetration testing
What's included?
- Robot Asset Access
- Deep Penetration Testing
- Solution-Oriented Reporting
Contact Us To Make an Appointment
Network Solutions
Comprehensive Network Solutions
What's included?
- Network Assessment
- Network Design
- Network Implementation
- Network Monitoring
- Documentation
- Regular Reporting & Reviews
Depends Of The Size
Dark web Monitoring
Intech Extra Add Ons
What's included?
- Dark Web Scanning
- personal credentials against the dark Web
Depends Of The Size
Latest blog articles about cyber security
Unlocking Efficiency: Essential Tips and Tricks for IT Users
In the dynamic world of Information Technology (IT), knowledge is power. Whether you’re a tech…
How Phishing Can Destroy an Organisation
In the vast expanse of the digital world, one of the gravest threats lurking in…
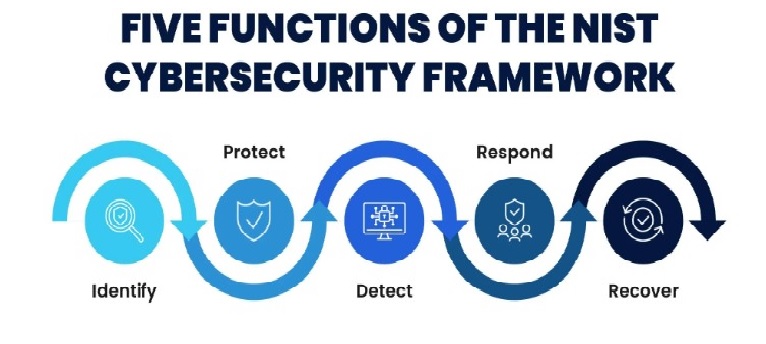
NIST: A Deep Dive into Cybersecurity Excellence
In today’s interconnected world, cybersecurity is more than just a buzzword—it’s a necessity. From personal…